Who should attend?
Those who are involved in, or responsible for a company’s IT infrastructure:
Credit Towards Certification: ECSA v10
Number of Questions: 150
Passing Score: 70%
Test Duration: 4 Hours
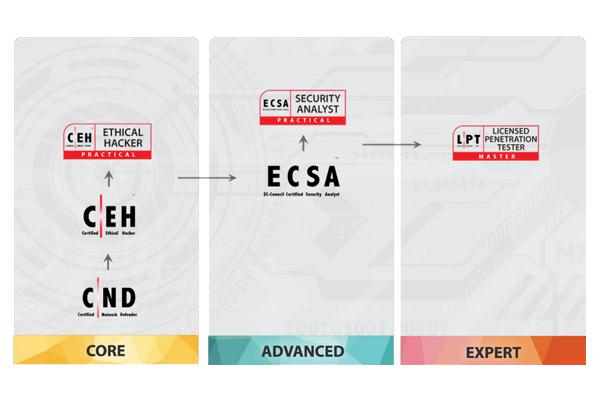
EC-COUNCIL CERTIFIED SECURITY ANALYST (ECSA)
The ECSA program offers a seamless learning progress, continuing where the CEH program left off.
Unlike most other pen-testing programs that only follow a generic kill chain methodology; the ECSA presents a set of distinguishable comprehensive methodologies that are able to cover different pentesting requirements across different verticals.
Who should attend?
The ECSA course is a fully hands-on program with labs and exercises that cover real world scenarios. By practicing the skills that are provided to you in the ECSA class, we are able to bring you up to speed with the skills to uncover the security threats that organizations are vulnerable to.
This can be achieved effectively with the EC-Council iLabs Cyber Range. It allows you to dynamically access a host of Virtual Machines preconfigured with vulnerabilities, exploits, tools, and scripts from anywhere with an internet connection.
Our guided step-by-step labs include exercises with detailed tasks, supporting tools, and additional materials as well as our state-of-the-art “Open Environment” allowing you to launch a complete live range open for any form of hacking or testing.
Module 00: Penetration Testing Essential Concepts (Self-Study)
Module 01: Introduction to Penetration Testing and Methodologies
Module 02: Penetration Testing Scoping and Engagement Methodology
Module 03: Open-Source Intelligence (OSINT) Methodology
Module 04: Social Engineering Penetration Testing Methodology
Module 05: Network Penetration Testing Methodology – External
Module 06: Network Penetration Testing Methodology – Internal
Module 07: Network Penetration Testing Methodology – Perimeter Devices
Module 08: Web Application Penetration Testing Methodology
Module 09: Database Penetration Testing Methodology
Module 10: Wireless Penetration Testing Methodology
Module 11: Cloud Penetration Testing Methodology
Module 12: Report Writing and Post Testing Actions
About the Exam
Ethical Hackers
Penetration Testers
Network server administrators
Firewall Administrators
Security Testers
System Administrators and Risk Assessment professionals